What is SonarHost.exe
SonarHost.exe is an executable exe file that comes with ESN Sonar API developed by Esn Social Software Ab Developers.
The .exe extension of the file SonarHost specifies that it is an executable file.
Malwares and virusus are also transmitted through exe files. So we must be sure before running any unknown executable file in our computer.
We will check if the SonarHost.exe file is a virus or malware? Whether it should be deleted to keep your computer safe? Read more below.
Is SonarHost.exe safe to run? Is it a virus or malware?
Let’s check the location of this exe file to determine whether this is a legit software or a virus. The location of this file is
Location : C:\Program Files\Battlelog Web Plugins\Sonar
SonarHost.exe Uninstaller : C:\Program Files\Battlelog Web Plugins\Sonar\esnsonar_uninstall.exe
To check whether the exe file is legit you can start the Task Manager. Then click on the columns field and add Verified Signer as one of the columns.
Now look at the Verified Signer value for SonarHost.exe process if it says “Unable to verify” then the file may be a virus.
| File Name | SonarHost.exe |
| Software Developer | ESN Sonar API |
| Publisher | Esn Social Software Ab |
| SHA1 | 3E0DB105D8BBE134C5B4860073348E6D99139D2F |
| MD5 | 533a078d98dd31c0a48d6795e0b61fca |
How To Remove or Uninstall ESN Sonar (SonarHost.exe)
To remove the SonarHost.exe from your computer do the following
- Run the uninstaller located at C:\Program Files\Battlelog Web Plugins\Sonar\esnsonar_uninstall.exe
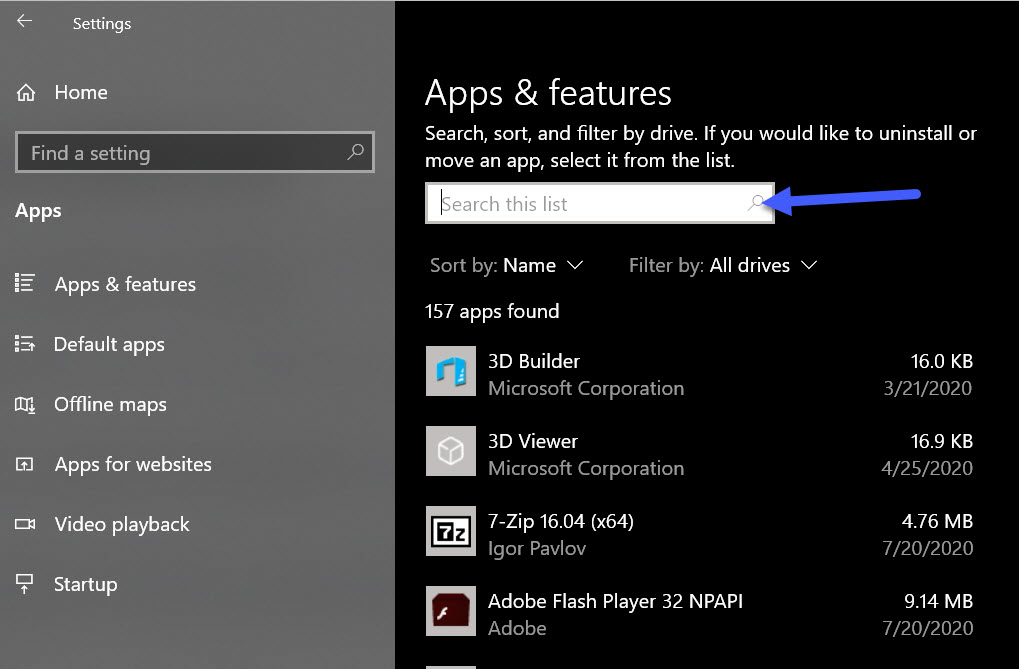
- Or Go to System settings and open Add or remove programs.
- Search for SonarHost.exe in the search bar.
- Click on Uninstall Program to remove SonarHost.exe file from your computer.
I hope you were able to learn more about the SonarHost.exe file and how to remove it.
Let’s us know in the comments below if you face any other SonarHost file issues.

He is the founder of howtodoninja.com and is an experienced tech writer and a cybersecurity enthusiast with a passion for exploring the latest technological advancements. He has 10 years of experience in writing comprehensive how-to guides, tutorials, and reviews on software, hardware, and internet services. With an interest in computer security, he strives to educate users by writing content on how to use technology, and how to also protect their smart devices and personal data from cyber threats. He currently uses a Windows computer, and a Macbook Pro, and tests hundreds of Android phones for writing his reviews and guides.